Top 7 Security features of Microsoft Cloud
July 21, 2023

Introduction
Since the COVID-19 pandemic began, many companies have shifted to cloud migration to enable remote work for their employees. However, this raises concerns about the security of sensitive business data. To safeguard their businesses, it is crucial to adopt a reliable Microsoft Cloud Security solution.
Among the many cloud security vendors in the industry, Microsoft Azure stands out as a leading player, which is adopted by 80% of Fortune 500 companies, namely HP®, FedEx, Walmart, etc. To maintain the highest levels of security, Microsoft has recently announced an extraordinary investment of $20 billion over the next five years to bolster the protection of its cloud services.
In this blog, we’ll explore the top 7 Security features of Microsoft Cloud, and find out the reasons why Azure services are suitable for not only large enterprises, but also small businesses. Let’s get started!
What are the Security features of Microsoft Cloud?
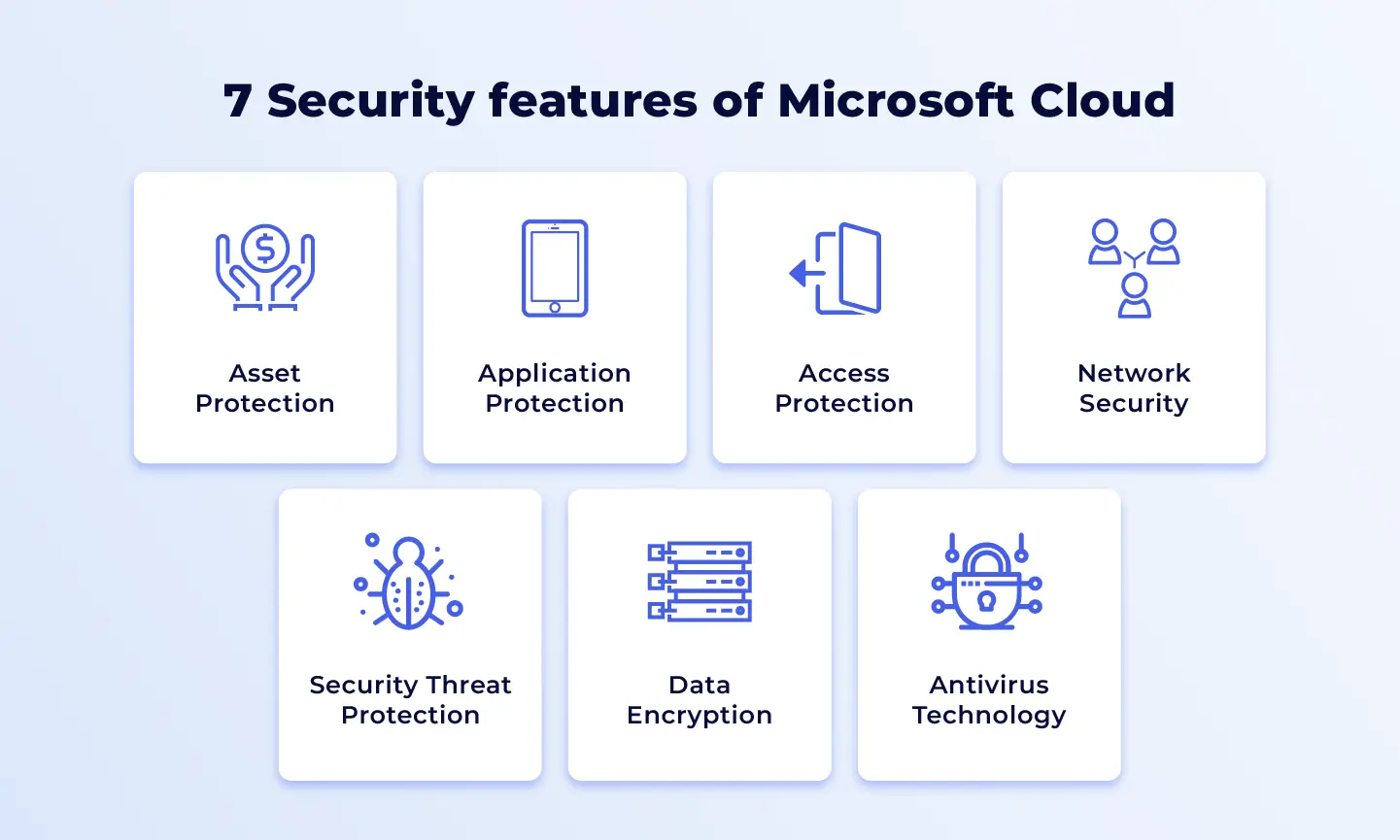
To secure its cloud ecosystem, Azure implements multiple-layered security, combining its own built-in security solutions with the option to integrate third-party security tools. This approach fortifies the cloud environment against a broad spectrum of threats, offering users peace of mind and a robust security foundation for their business operations. Azure security features are listed as follows:
Asset Protection
Asset protection in the Microsoft Cloud refers to safeguarding the physical and virtual resources, such as servers and data storage, at their core level of availability. When users use services like Azure Virtual Machines and Azure Storage, these assets are automatically protected through replication.
The Azure infrastructure is built with a focus on high availability, efficiency, and redundancy for its fundamental computing and storage components. Unlike traditional on-premises IT environments, where ensuring reliability and availability can be costly and complex, the cloud infrastructure handles these aspects automatically.
By replicating data and utilizing redundancy, the cloud provides significant benefits in terms of data protection and continuous availability. However, for end-users, effectively managing the usage and access to these valuable IT resources in the cloud would be a huge challenge.
Application Protection
In the Azure cloud, applications can be managed either as standalone Software as a Service (SaaS) offerings or as part of a larger suite of services and software. Microsoft applications, such as Microsoft 365, OneDrive for Business, Teams, SharePoint, etc, come with automatic protection features. Microsoft also offers comprehensive cloud applications and data protection alternatives to users. These measures are in place to ensure the security and integrity of the applications and data stored in the cloud.
However, it’s essential for businesses to understand that while Microsoft provides protection for the applications, users should be responsible for their stored data, which includes taking proper backup procedures to safeguard the data. Users should also be mindful of who has access to their applications. Controlling app access ensures that only authorized personnel can use them, reducing the risk of unauthorized access or data breaches.
Access Protection
Access protection in the cloud involves managing user access to resources, and it’s divided into three categories:
Active Directory Services: These services manage information about users and their permissions stored in directories. System administrators use these services, along with Two-Factor Authentication (2FA), to enhance security and control access to different parts of the information.
Identity and Access Management (IAM): IAM is a web service that helps store user information. It is utilized by various services, including Active Directory, to control who is allowed to authenticate and access infrastructure, systems, and applications.
RBAC (Role-Based Access Control): Azure RBAC is a system used to grant permissions to users based on their defined roles within the organization. This ensures that users only have access to the resources necessary for their responsibilities.
The cloud provides a great advantage to end users by offering infrastructure for robust access controls as a service. However, it’s essential to understand that even with this infrastructure in place, significant expertise is still required to effectively manage access and control in the Microsoft Cloud. This expertise ensures that access is properly configured, reducing the risk of unauthorized access and potential security breaches.
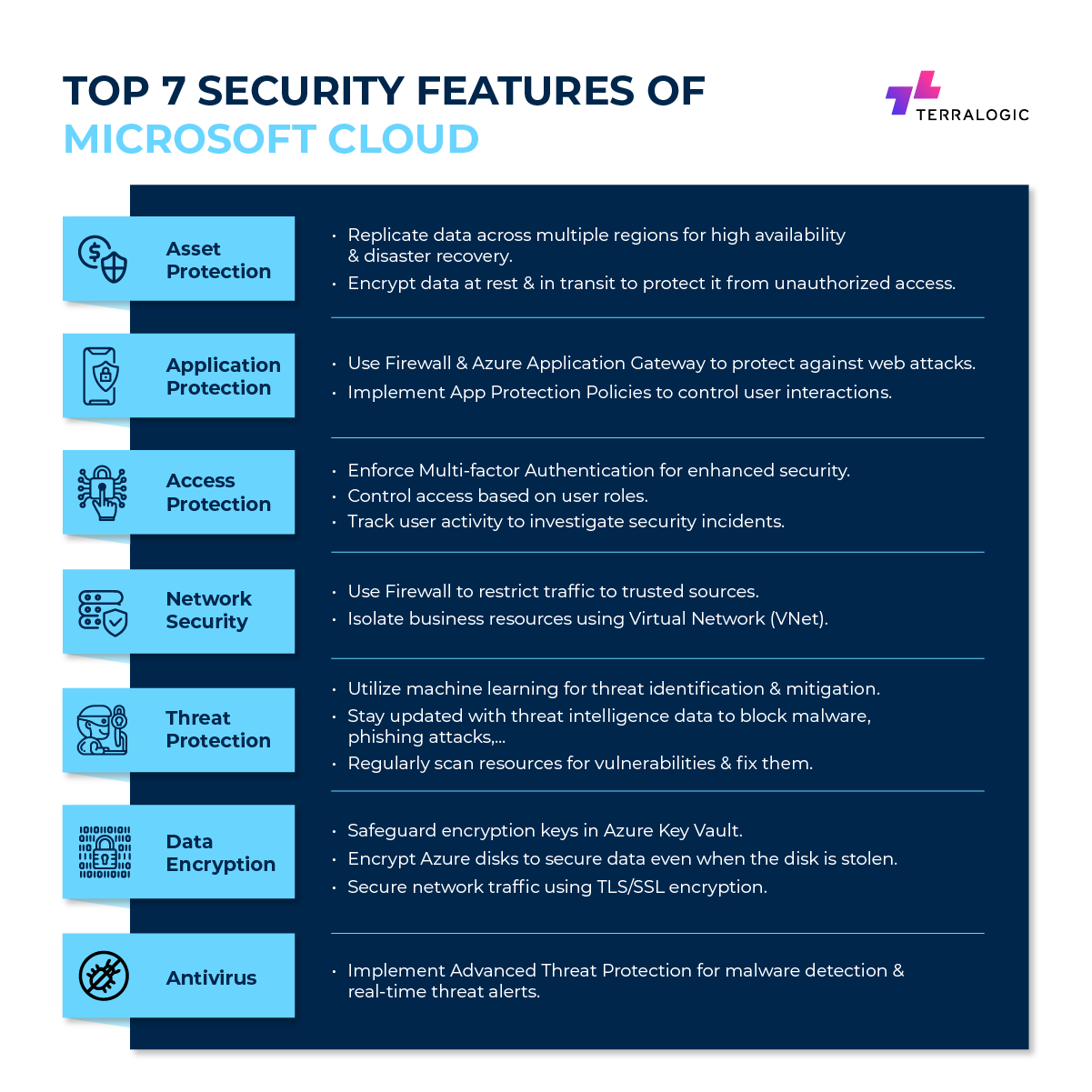
Network Security
Network security is a top priority for Microsoft’s cloud platform, and they invest heavily in this area. Every year, Microsoft allocates over $1 billion and employs more than 3,400 cybersecurity professionals to ensure its cloud service security. As a result, all resources deployed in the Microsoft Cloud benefit from a high level of network protection, which is impossible to replicate outside of the cloud environment. Given that, end users who use Microsoft Cloud Azure can take advantage of security measures to protect the data and resources within their cloud infrastructure.
However, it’s important to note that while Microsoft ensures security within its cloud platform, end users are still responsible for designing, building, and maintaining their own internal and external network infrastructure for private usage. This means that users need to take care of the security of their own networks, including setting up firewalls, managing access controls, and implementing other security measures, to protect their data and systems outside of the Microsoft Cloud environment.
Security Threat Protection
The Microsoft Cloud provides comprehensive security threat protection for organizations, safeguarding them from various types of attacks at a large scale. The platform has measures in place to prevent Distributed Denial of Service (DDoS) attacks, HTTP attacks, volumetric attacks, SQL protocol attacks, and other types of cyber threats.
To protect against user-level cyber attacks, such as Phishing and Ransomware, Microsoft has also integrated security features within applications like Exchange and Office 365. These built-in protections help identify and mitigate potential security threats, enhancing the overall security of user data and communications.
For even more robust security, Microsoft offers a pay-for-use application called Defender for Cloud. This application provides both basic and advanced security features specifically designed to protect Azure resources. By using Defender for Cloud, organizations can further strengthen their security posture and safeguard their assets within the Microsoft Cloud environment.
Data Encryption
Data encryption is a crucial security measure provided by Microsoft Azure to protect your data. It ensures that your data remains secure both while it’s being transmitted across networks (encryption in transit) and when it’s stored in Azure (encryption at rest).
Encryption in transit: When your data is sent over networks, whether within Azure or to your employees’ devices, all files are completely encrypted. Even if someone tries to intercept the data during transmission, it would appear as scrambled and unreadable to them. This ensures that your sensitive information remains safe from prying eyes.
Encryption at rest: When data is stored in Azure storage, it can be encrypted. This means that even if someone gains unauthorized access to the physical storage disks, they wouldn’t be able to read the data without the proper security keys. In other words, the data remains protected even if the storage media, like a disk, is stolen or hacked into.
Antivirus technology
In addition to Microsoft’s own built-in antivirus and anti-malware software, antivirus solutions from third parties like McAfee, Kaspersky Labs, Symantec, etc are great options for users to add an extra layer of protection to virtual machines. These third-party solutions continuously scan for potential malware and other threats, ensuring that your Azure environment remains secure from any potential breaches.
Why is Microsoft Azure suitable for Small Businesses?
For small to medium-sized businesses (SMBs), the challenge of managing services and ensuring constant uptime can be overwhelming. Handling all this information in-house can lead to problems, as it requires significant manpower and space to maintain security and reliability. Therefore, SMBs should consider adopting a secure cloud service to control security threats effectively. However, why should it be Microsoft Azure?
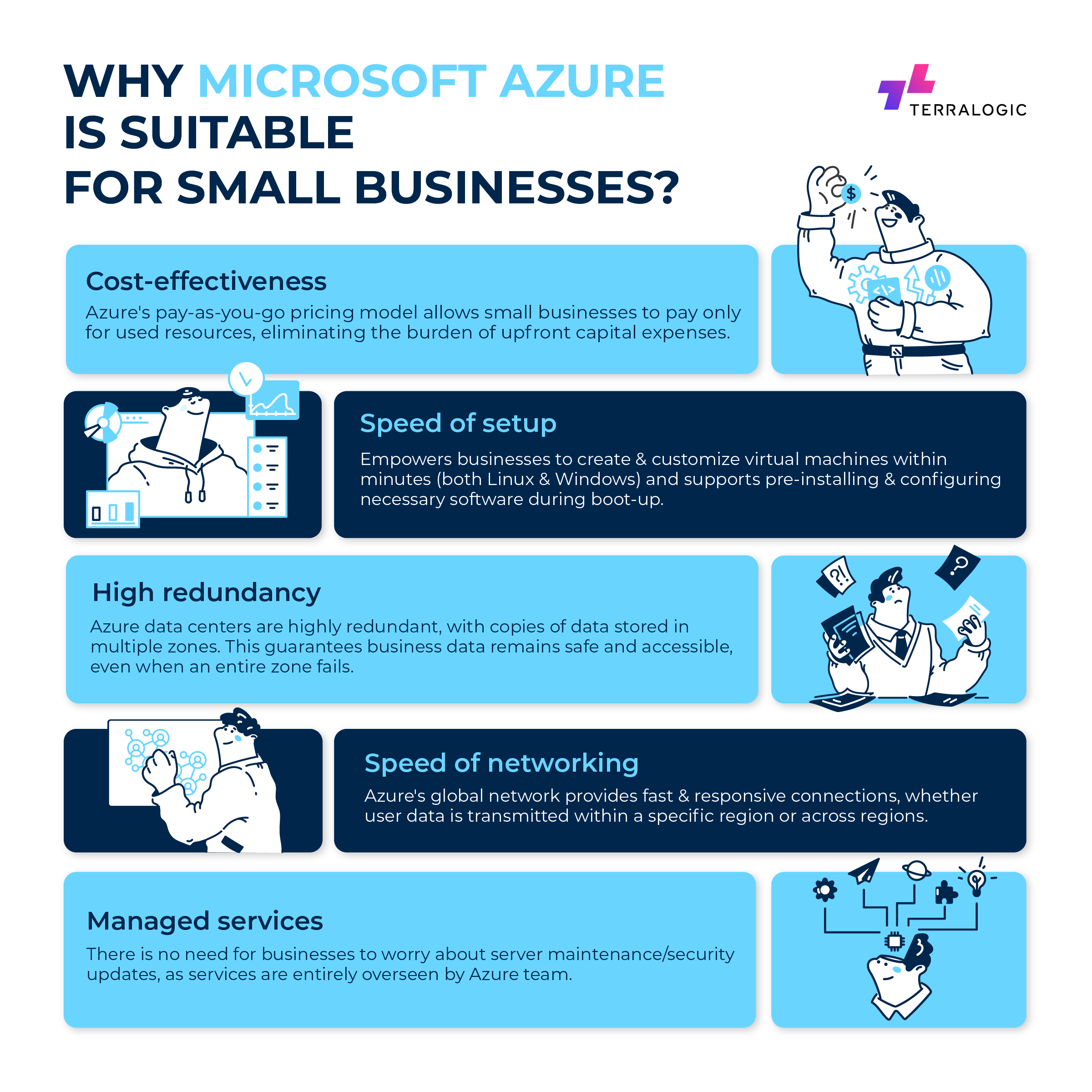
Cost-effectiveness: Azure’s pay-as-you-go model allows SMBs to pay only for the resources they use, which enables cost optimization and eliminates the burden of upfront capital expenses. Moreover, as Microsoft purchases a large number of machines annually, small businesses can access these machines at significantly reduced costs compared to buying them individually.
Speed of setup: Azure enables small businesses to respond quickly to changing demands without unnecessary delays or expenses. Within minutes, businesses can create and customize a virtual machine with their operating system, whether it’s Linux or Microsoft Windows. In addition, a tool called “cloud-init” allows these virtual machines to be pre-installed and configured with the necessary software during the boot-up process. This means no more waiting for weeks or months to increase capacity, and there’s no need to over-purchase machines in case of unexpected server traffic.
High redundancy: Azure’s data centers are highly redundant, with multiple availability zones and copies of data stored in different locations. This process guarantees that even if an entire zone within an Azure region were to fail, the data remains safe and accessible from the redundant copies in other zones.
Speed of networking: Microsoft Azure’s global network presence provides fast and responsive connections to end users. Within a specific region, data can be transmitted at incredible speeds, ranging from tens to hundreds of gigabits per second. Even when data is transmitted between different Azure regions, the network’s backbone maintains high-speed connections, often reaching gigabits per second or even faster rates. This robust network infrastructure ensures efficient data transfer and a seamless experience for businesses and their customers worldwide.
Managed services: Small businesses benefit greatly from Microsoft Azure’s managed services. For example, Azure SQL Server is entirely overseen by the dedicated Azure SQL team. This means small businesses don’t need to worry about maintaining and updating the underlying servers or SQL software for security. Beyond database services, Microsoft Azure also manages other critical aspects, such as storage accounts, streaming analytics services, etc.
Final thoughts
Without a doubt, cloud services offer built-in security features and benefits that traditional IT setups lack. Microsoft, in particular, is heavily investing billions of dollars in both infrastructure and human resources to create an exceptional and secure computing environment for its users.
However, it’s essential for end-users to be aware that while the cloud provides powerful security capabilities, successfully utilizing and managing these services requires a certain level of expertise. The cloud environment involves numerous components and complexities that need to be configured correctly to ensure smooth operations and optimal security.
Given that, if you are still worried about managing your cloud, Terralogic will all in place to help you. We have the solid experience and expertise to instantiate the promise of the cloud to end-users of all scales and scopes. We aim to optimize a variety of services of the Microsoft Cloud to provide a secure, cost-effective, efficient, seamless digital experience for you and your users.
Are you ready to engage with our team of IT experts to discuss affordable, optimized IT strategy and management? Let’s get in touch with our team today!
Keep reading about
LEAVE A COMMENT
We really appreciate your interest in our ideas. Feel free to share anything that comes to your mind.




