Program Structure
Trimester I
- Information Security and Cybersecurity
- Threat Landscape
- Vulnerability Assessment & Penetration Testing (VAPT)
- Cyber-Attack Scenarios
Trimester II
- Incident Management
- Security Intelligence Analyst with IBM QRadar SIEM
- Working with QRadar
Trimester III
- Incident Response Processes
- Incident Response Management : Tools, Techniques, SOC
- Incident Detection Scenarios
- Remediation and Reporting
- Security Analytics
Trimester IV
- Threat Hunting and Descriptive Analytics
- Predictive Analytics in Cybersecurity
- Machine Learning Applications in Cybersecurity
- SIEM Scenarios
Trimester V/VI
- Cybersecurity Frameworks
- Working with SOC
- SOC Management – Investigation and Analysis
- Trimester V & VI
- Capstone Projects
Learning Outcomes
An outcome-driven program based on skill and only skill designed for working professionals to heighten their careers in their intermediate and senior roles in security-related areas. Hence, the course is practical and lab-based practices, either proprietary or open software used in the market today. We offer Online LMS and Assessments.
At the end of the program, you get to:
- Identify and assess security risk
- Perform risk analysis
- Uncover potential vulnerabilities
- Protect the enterprise IT assets
- Develop security policies and procedures
- Monitor and detect threats
- Establish a robust response plan
- Recover, restore, and prevent future attacks
Security Operations Centre (SOC)
The partakers will get to work with a live SOC (Security Operations Center, rendering real-time experience in detecting, analyzing, and responding to incidents using a combination of technology solutions and a robust set of methods.
- Incident Response
- Network Security
- SIEM Log Monitoring
- Identity & Access Management
- Compliance Analysis & Reporting
- Threat & Vulnerability Management
- Vulnerability Assessment & Penetration Testing
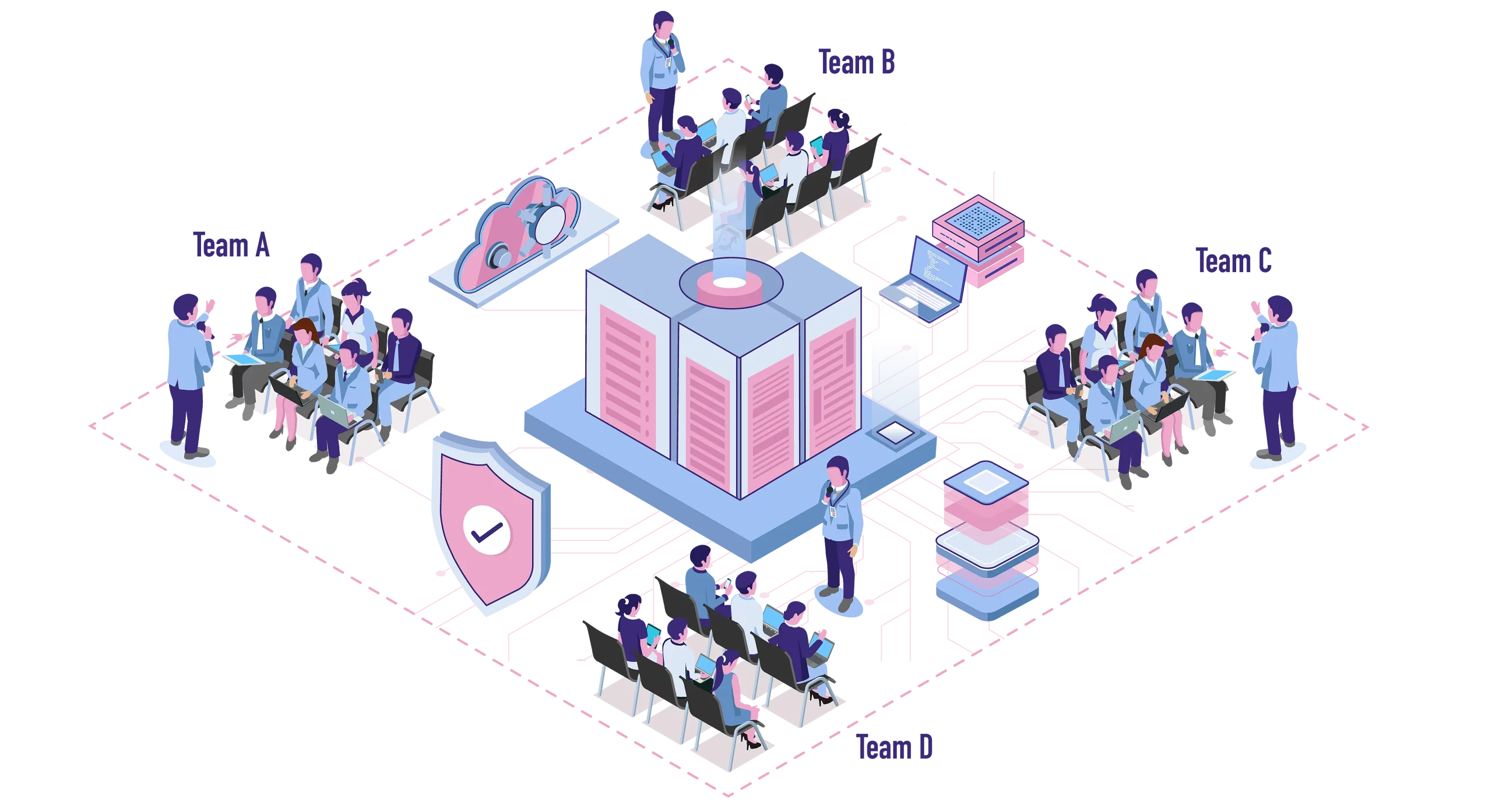
Exclusive Cyber Range as Simulator
Cyber Range is an infrastructure stationed to generate a real foundation – like a test lab – to train your team(s) to protect against cyber-attacks scenarios. The partakers will get access to this virtual environment on cyber warfare scenarios during the program, just like the infographic.
Mentors

Sandeep Vijayaraghavan K
Vice President - Cybersecurity Practice, Terralogic

Ram Kumar G
CISM, CRISC, CEH, CPISI, BCCE

Aditya Jain
Manager, PwC India

Chinmay Hegde
Chief Partner, Astrikos Consulting

Sridhar Govardhan
CISO, Wipro Limited

Ajay Pandey
Cybersecurity Solutions Architect – Advanced Services, Cisco
Industry Connect
Terralogic provides Cybersecurity career-enhancing prospects in association with REVA Academy for Corporate Excellence (RACE). The program participants, after successful complications of the courses, students attract various career-enhancing opportunities, including lateral placements, promotions, salary hikes, and transformation into professions in data science, analytics, cybersecurity, and other emerging technology domains.
Our 16 years of achievements includes:
-
10M+
lines of codes
-
2400+
projects completed
-
900+
satisfied clients
-
16+
countries served































